
To enhance information security and mitigate potential privacy and security breaches, BCIT is introducing multi-factor authentication (MFA) for students on BCIT systems. This implementation will involve using Microsoft Authenticator, which will add an extra authentication step in certain circumstances when logging in.
General questions about MFA and Microsoft Authenticator
Multi-factor authentication (MFA) means using more than one “factor” to verify a user’s identity at a login point. Previously, BCIT was using single-factor authentication – where that single factor was your usual BCIT password – to confirm that you are who you say you are when you try to login to a BCIT system or tool.
With the transition to MFA, the process will still begin with your usual BCIT login credentials (your myBCIT email address and password). However, we will now include an additional factor for verification. This will typically involve either accessing an enrolled mobile app on your smartphone to confirm your login attempt or using a device (SafeID token) that can provide a passcode. The additional authentication step is an added layer of security on top of your existing credentials.
Login credentials are valuable and are increasingly easy to compromise. Over 90% of breaches today involve compromised usernames and passwords. A majority of cybersecurity incidents have come from compromised passwords, and MFA is designed to reduce this risk. By requiring two different channels of authentication, your login credentials are protected from remote attacks. MFA prevents anyone but you from accessing your account, even if they know your password.
You will be prompted for MFA when you sign into most web applications and/or services at BCIT, including:
- Microsoft365 Office (web and desktop client)
- OneDrive (web and desktop client)
- Apporto
- AppsAnywhere
- Azure Labs
- Learning Hub
- myBCIT
Not ordinarily. In most cases you are able to check an option to remember any specific device for 90 days. As a result, most users can choose do only do MFA occasionally, depending on how they interact with BCIT systems. Users who utilize multiple devices or browsers, who frequently access a variety of applications, or who commonly use incognito/private browser windows, frequently restart, etc., may need to do MFA a little more often. As well, you will not generally be asked to do MFA if you are on campus and connected to BCIT wifi or wired networks.
The simplest option, and the one BCIT recommends, is to install the Microsoft Authenticator Mobile app on your personal iOS or Android phone or tablet. With this app, once you’ve gone through the initial setup process , you can quickly confirm that you are the person attempting to log into your account. You are likely already carrying your phone with you, so having it available whenever you need to access an affected BCIT system is likely to be the easiest method to use.
There are also other options that you could use instead of or in addition to the Microsoft Authenticator phone app, such as a SmartID hardware token (available at the BCIT bookstore), adding the Microsoft Authenticator app to a second device, using a YubiKey, or others. You can have multiple methods set up at the same time to increase the likelihood of having a method available when you need one (including when your phone battery is dead). You would need to carry at least one method with you whenever you anticipate needing to access an affected BCIT system.
In the event that you find yourself without an MFA method and require access to a protected BCIT system, the IT Service Desk can offer a bypass as a last resort. Please note: this is only available during listed service hours.
Follow the instructions in the Setting up Multi Factor Authentication for Students article.
Starting August 25, 2025, employee and student accounts will be separated. This change strengthens access management, ensures each account only connects to its intended systems, and enhances the protection of your data and cybersecurity at BCIT.
If you’ve already set up MFA for your student email account, you will need to complete a separate MFA setup for your employee email account.
For more information, please refer to the following articles:
Troubleshooting
First of all, if you’re on campus and connected to BCIT networks or using a BCIT lab computer, you’ll (almost) never be asked to MFA. And if you’re using your own personal device and have asked MFA to remember that device anytime in the last 90 days, you shouldn’t be asked to MFA again on that device (as long as you’re using the same browser/aren’t attempting to connect to something within a private browser window/etc.) until that 90 days is up. So, depending on your situation and decisions you made in the past, it’s possible that you won’t need your MFA device or token before you can get back to your phone/token.
In the event that you find yourself without an MFA method and require access to a protected BCIT system, the IT Service Desk can offer a bypass as a last resort. An analyst, once they’ve verified your identity, can provide you with a temporary MFA bypass. This is only available during listed service hours, so again, we strongly recommend setting up more than one MFA method and keeping at least one method with you whenever you may need to connect to an affected BCIT system.
If you have more than one MFA method setup, you can remove the lost mobile device or SafeID token yourself.
If the method you lost is the only method you had, you will need to contact the IT Service Desk for assistance.
If you no longer intend to use your SafeID token and wish to transfer it to another user, you must start by removing your SafeID token from your list of MFA methods. Afterwards, the new user can follow the necessary steps to set up their SafeID token.
In case you encounter any difficulties while trying to remove your SafeID token, please reach out to the IT Service Desk for assistance. They will require your information and permission to process the changes.
Note: If you do not remove the SafeID token from your list of MFA methods, the new user will be unable to utilize it.
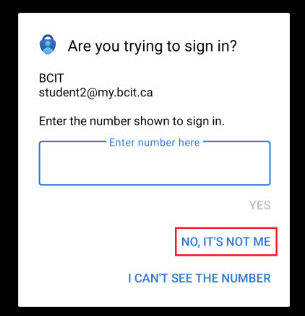
If you receive an authentication request that you did not initiate, and especially if you receive more than one, it’s best to report the suspicious activity.
- Click on No, it’s not me.
- Click on Report.
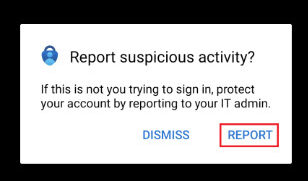
Once you do this, your account will become locked and you will see an error if you attempt to login.
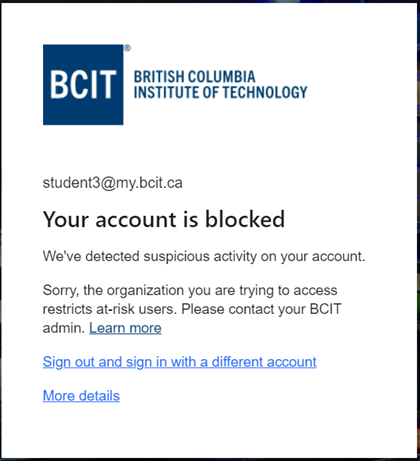
To unblock your account, change your password and the block will be removed automatically within 30 minutes. Alternatively, if you require access immediately, contact the Service Desk and explain the situation. They can verify that your account is blocked and expedite your return to access.
If you’ve already gone through the steps to add the App to your device and enroll it, there are several possible reasons why you may not receive notifications:
- You haven’t turned on notifications for the Microsoft Authenticator app on your phone.
- Your phone has no connection to the internet (wifi, cellular, etc.).
- Your phone is not connected to wifi and you haven’t permitted the app to use your cellular data.
- Your phone is in a state in which it cannot receive or notify you about the login attempt (powered off, airplane mode, “do not disturb” or similar status, etc.).
One possibility is that a Focus profile is preventing it. This is a feature introduced in recent versions of iOS.
Depending on your settings, your active Focus profile can suppress Microsoft Authenticator app notifications and prevent you from seeing them. To prevent this, add Microsoft Authenticator to the “Allowed Notification Apps” in all relevant Focus profiles.
If the Microsoft Authenticator app is not whitelisted in this manner, you won’t receive any Authenticator app notifications while using one of the Focus profiles. Consequently, this might lead to inadvertent lockouts due to multiple failed (timed out) MFA attempts.
If you have both phones available to you (or if you only have the new phone but already have other available MFA methods setup), simply go through the process to add your Microsoft Authenticator to your new phone, and then remove the old phone from your list of methods.
If you only have your new phone and your old phone was the only MFA method you had registered, you will need to contact the IT Service Desk for assistance.